we can use Cewl to generate passwords that might exist on the website itself.
cewl -w customWordsList.txt -d 4 -m 6 –with-numbers https://team1.pentest.id/
d means depth and m means minimum word count this will generate the file below
we can use Cewl to generate passwords that might exist on the website itself.
cewl -w customWordsList.txt -d 4 -m 6 –with-numbers https://team1.pentest.id/
d means depth and m means minimum word count this will generate the file below
The concept of “Google Hacking” dates back to 2002, when Johnny Long began to collect interesting Google search queries that uncovered vulnerable systems and/or sensitive information disclosures – labeling them googleDorks. some people call it googlehacking.
Simply search within google with the proper classifiers and you might be able to obtain information you might not otherwise get
a full command list is in the following database
we tried to perform msfexploit on the eternalblue vulnerability.
msfexploit is a tool to use the vulnerabilities using given payloads below is a search on eternalblue
then user should check by using the auxiliary to check if the target is the response
after confirming the target is vulnerable then we should input all the data into the Metasploit.
the screenshot is below shows the process being doen and set up a reverse_tcp connection with access to its cmd
Nmap is now one of the core tools used by network administrators to map their networks. The program can be used to find live hosts on a network, perform port scanning, ping sweeps, OS detection, and version detection
the command is
nmap (url)
Example is below
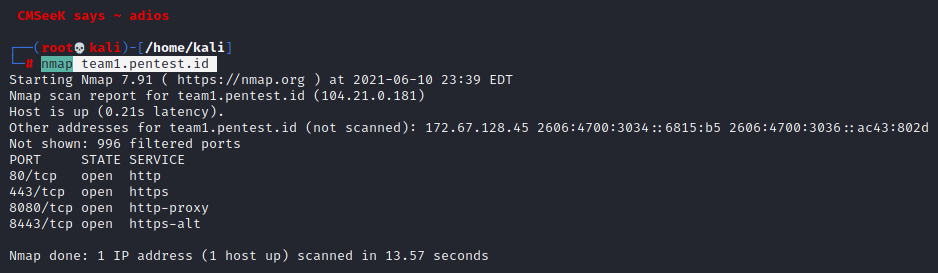
then it shows the open ports and other details for team1.pentest.id
Censys is an alternative to shodan doing similar results. it is used to find good server data recently.

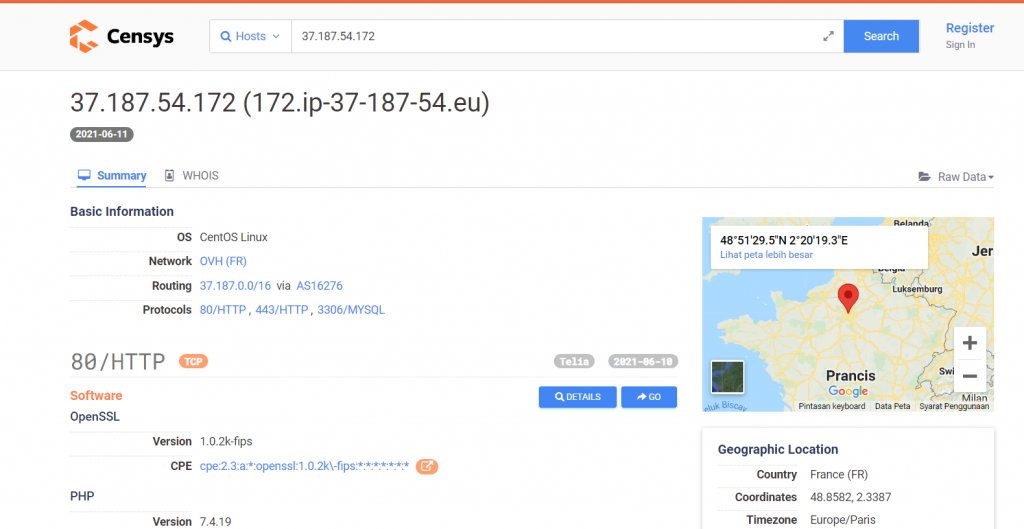
below is the overview explained by the official website
Censys maintains three datasets through daily ZMap scans of the Internet and by synchronizing with public certificate transparency logs:
Owasp ZAP
Owasp zap is an open-source web application security scanner. It is intended to be used by both those new to application security as well as professional penetration testers. it is used as a tool to detect the possible vulnerabilities of a system while also cross checking it through the owasp zap database.
The usage is very simple simply install it in kali Linux. and then open it then select automated scan for newer users then simply put in the url to attack then click the attack button
when done simply wait below is an example of the result with the data
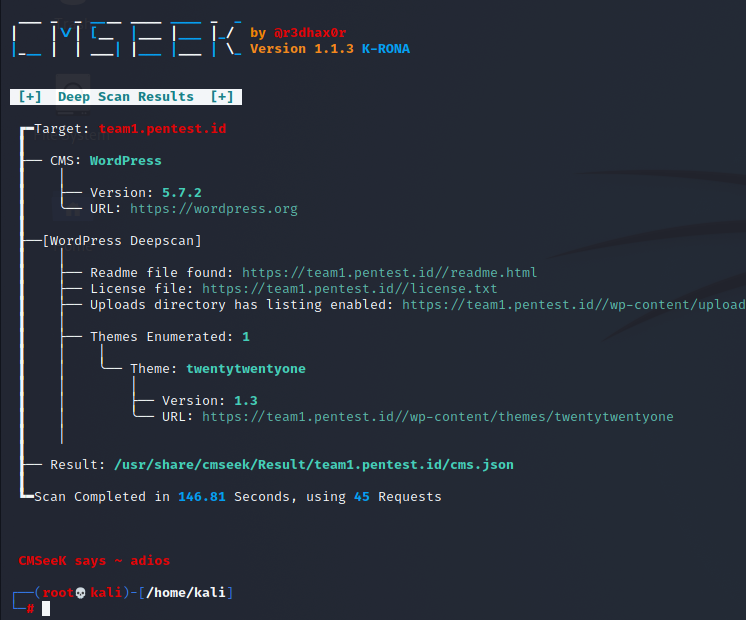
CMSeeK is a CMS detection and exploitation tool, written in Python3, capable of scanning numerous content management systems including WordPress, Joomla, Drupal, etc. It allows you to run both simple CMS detection and deep scans, as well as multisite scans. Currently it can be ran on any Unix-based system (Linux, OS X)

the above is a screenshot of CMSeek
we just choose number 1 and then simply wrote down teh target full url below are the results.
We learned how to use theHarvester in this lesson the description of the program is below
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
This tool is intended to help Penetration testers in the early stages of the penetration test in order to understand the customer footprint on the Internet. It is also useful for anyone that wants to know what an attacker can see about their organization.

the commands are simple
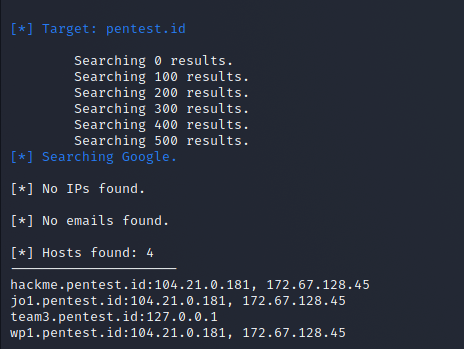
theHarvester -d pentest.id -l 500 -b google
the above means to search up pentest.id up to 500 limit on google. it will then search for relevant data for pentest.id below is the result
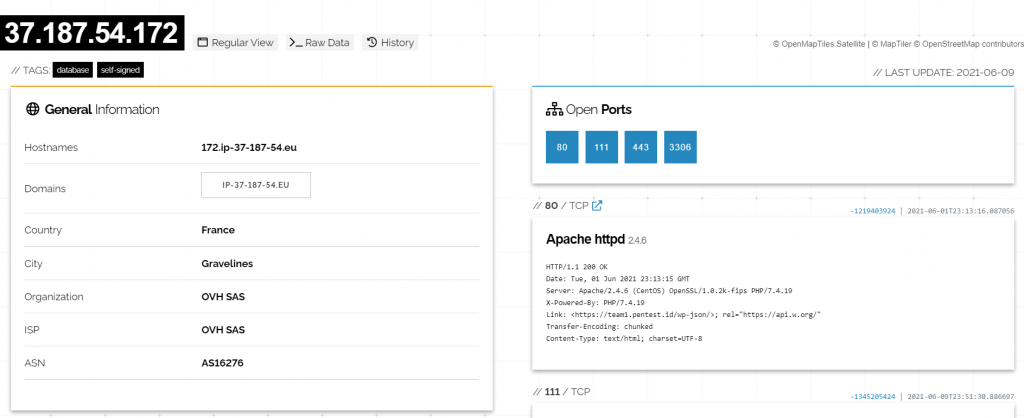
We use Shodan to access all the data that is available online regarding the data how to use it is simple
Open shodan.io and simply input the target.
Then it will give you all the data
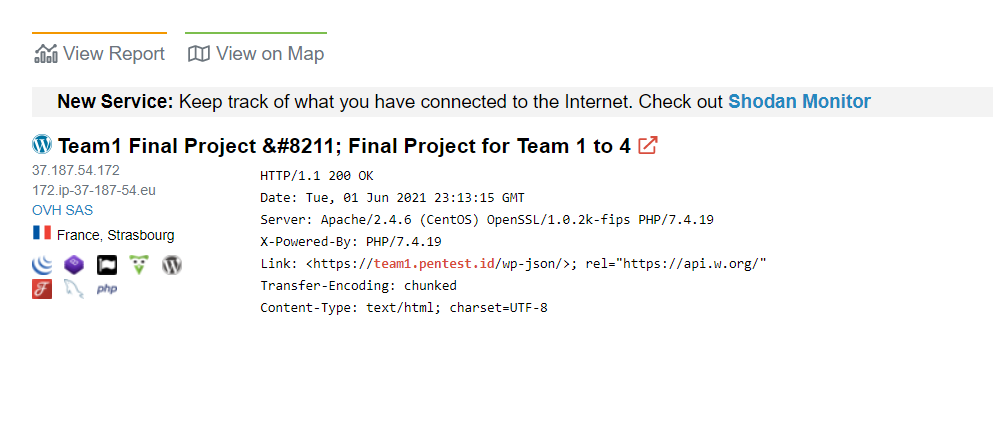
if you open it thne you get the other data incuding the ip behind cloudflar
Ethical hacking also known as penetration testing or pen testing, is legally breaking into computers and devices to test an organization’s defenses. It’s among the most exciting IT jobs any person can be involved in. You are literally getting paid to keep up with the latest technology and get to break into computers without the threat of being arrested.
The first week we did not try out anything but learned about script kiddies, hackers, crackers and all the others that definitions that are important.